 HackersvellA
HackersvellA
Moltbook: The Day AI Built Its Own World
Moltbook: The Day AI Built Its Own World
Read more →Latest Articles

HackersvellA
The Cyber Threat Landscape of 2026: Risks, Reality, and Resilience
The Cyber Threat Landscape of 2026: Risks, Reality, and Resilience
Read more
HackersvellA
CVE-2025-0247: The Firefox Vulnerability That Exposed Millions to Risk
CVE-2025-0247: The Firefox Vulnerability That Exposed Millions to Risk
Read more
HackersvellA
Massive Instagram Data Exposure Raises Alarms Over User Privacy and Security
Massive Instagram Data Exposure Raises Alarms Over User Privacy and Security
Read more
HackersvellA
Coupang Data Breach: South Korea’s Biggest Ever and a $1.2B Settlement
Coupang Data Breach: South Korea’s Biggest Ever and a $1.2B Settlement
Read more
HackersvellA
Even Space Isn’t Safe: Inside the European Space Agency Cyberattack
Even Space Isn’t Safe: Inside the European Space Agency Cyberattack
Read more
HackersvellA
Global Cyberattacks 2025: The $10 Trillion Wake-Up Call to the World
Global Cyberattacks 2025: The $10 Trillion Wake-Up Call to the World
Read more
HackersvellA
India’s Airports Hit by GPS Spoofing Cyberattacks
India’s Airports Hit by GPS Spoofing Cyberattacks
Read more
HackersvellA
OpenAI Data Exposure: What Really Happened in the Mixpanel Cyberattack (2025)
OpenAI Data Exposure: What Really Happened in the Mixpanel Cyberattack (2025)
Read more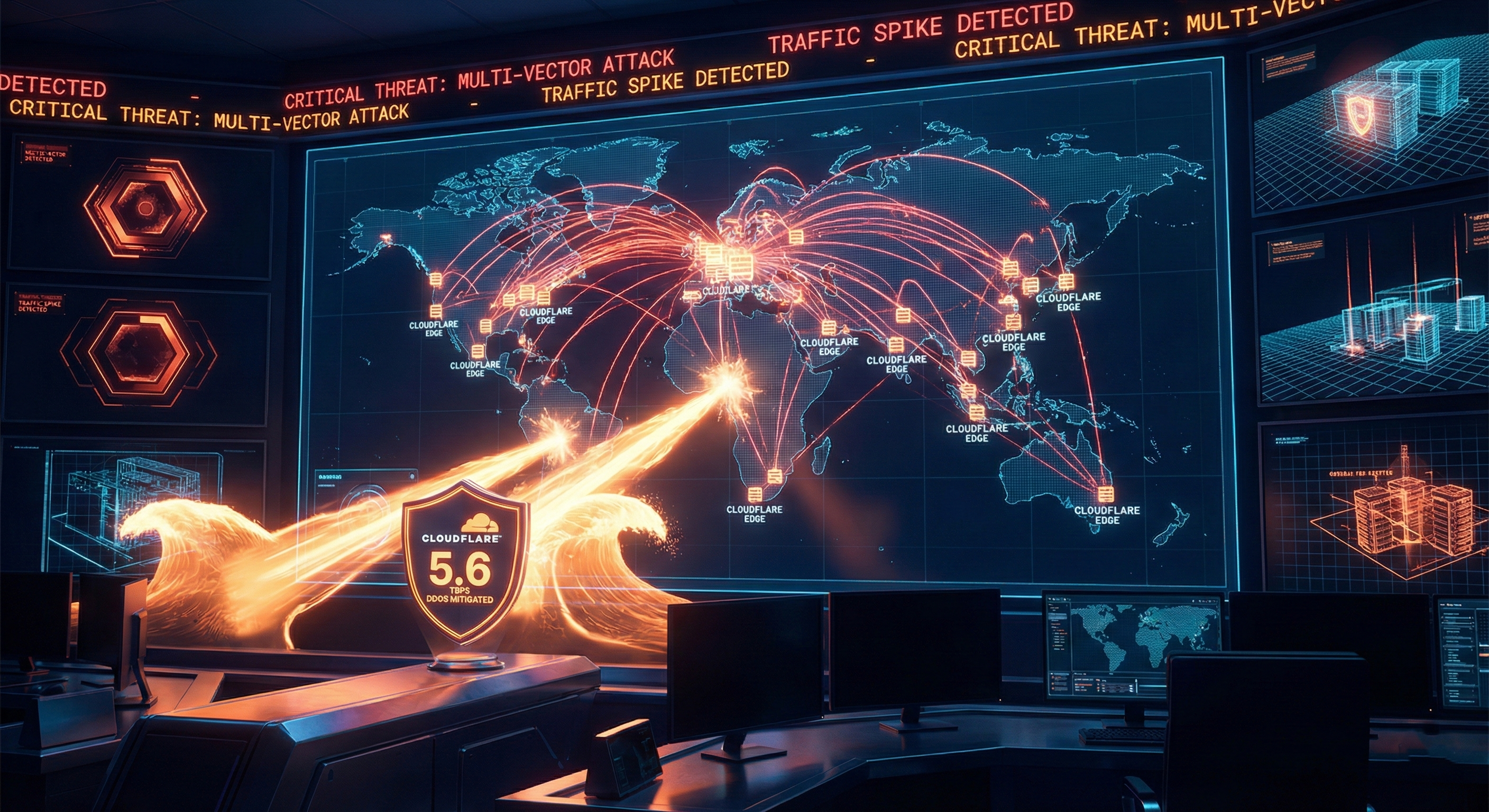
HackersvellA
Record-Breaking DDoS Cyberattack on Cloudflare: What Happened and Why It Matters
Record-Breaking DDoS Cyberattack on Cloudflare: What Happened and Why It Matters
Read more